Single Sign on with Azure AD
Configure Azure SSO with Fiddler
Prerequisite
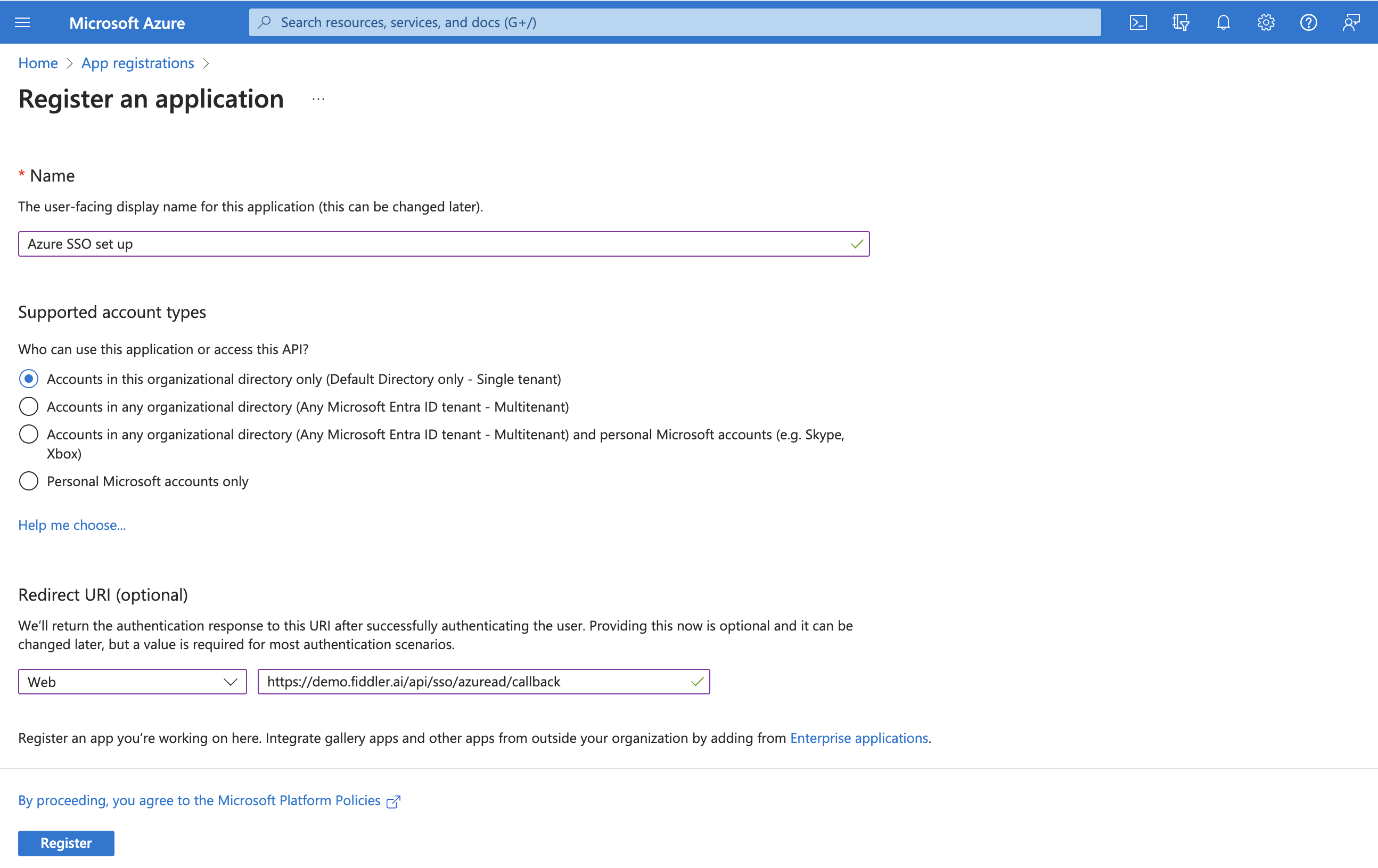
Set up OIDC configuration within Azure by selecting the type as Web and with the redirect URI pointing to your deployment, as seen in the image below.
Redirect URL - {base_url}/api/sso/azuread/callback
Once the registration is successful, create a new client secret and copy the secret value immediately after it is created without refreshing the page.
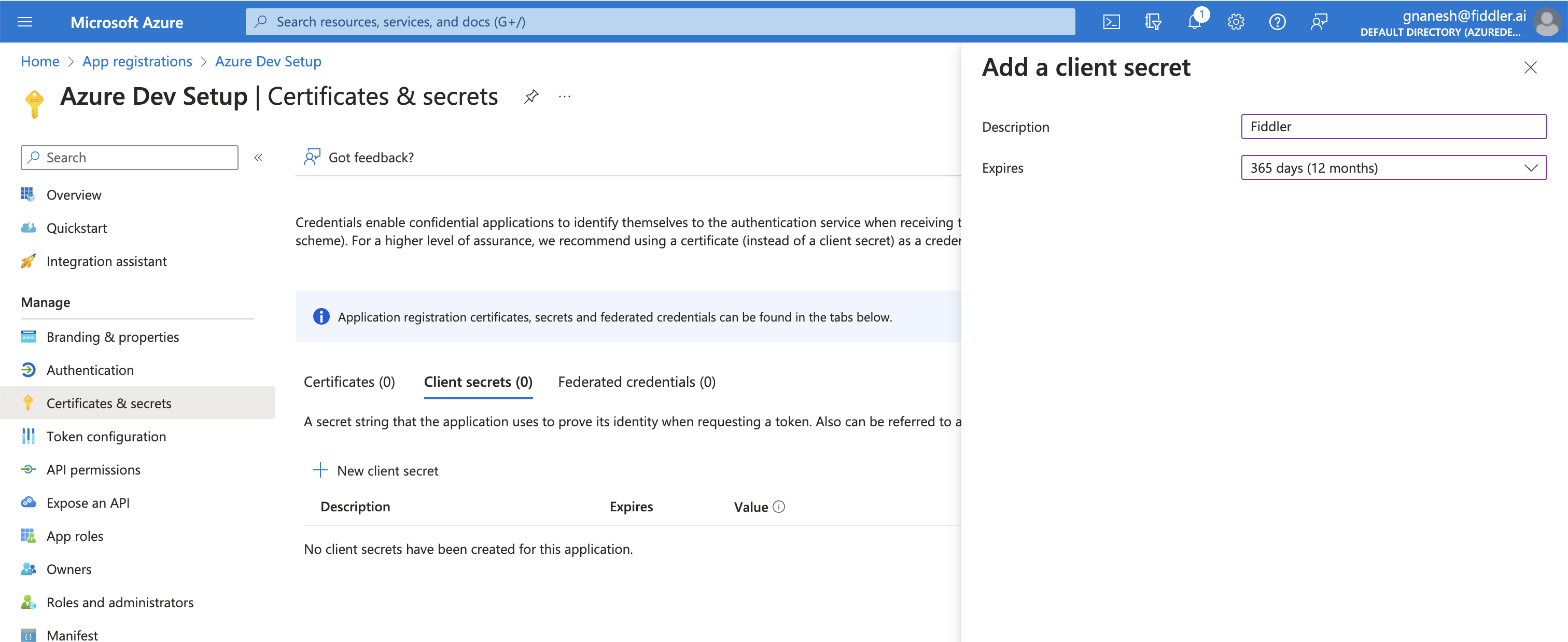
Be careful
You will not be able to access the
client secretlater because it is shown ONCE and not repeated
Creating a new client secret
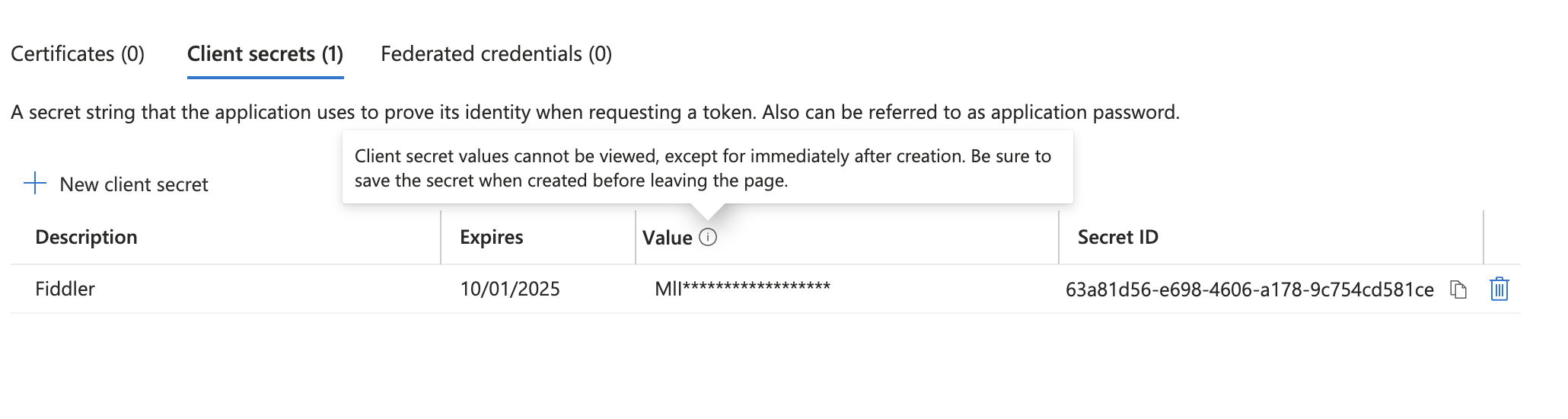
Masked client secret value
Configure Azure SSO with Fiddler
The following details are required
- OpenID Connect metadata document
sso-azuread-identity-metadata - Application (client) ID
sso-azuread-client-id - Newly created client secret
sso-azuread-client-secret
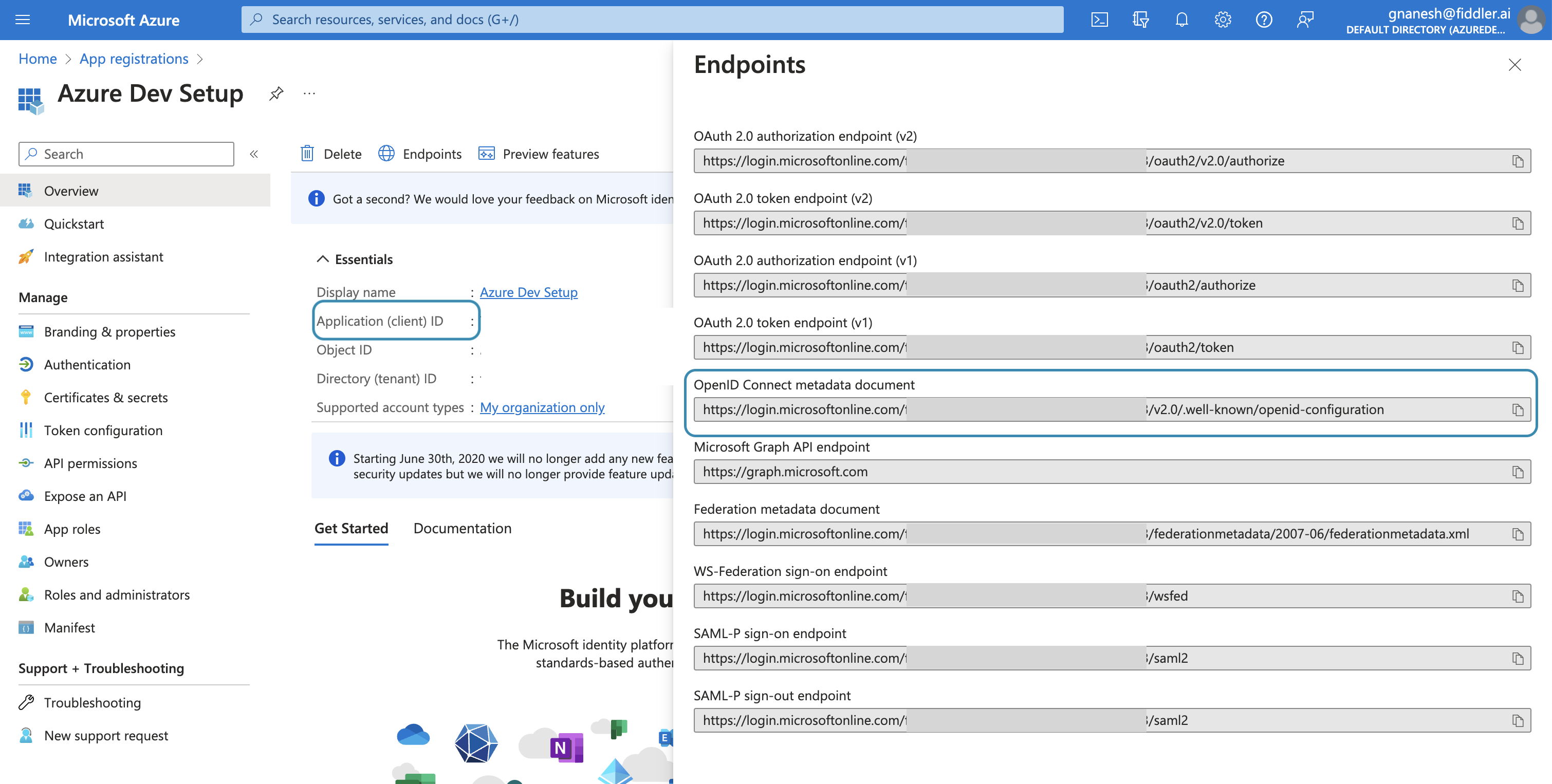
OpenID Connect metadata Document can be found under Endpoints under the overview section.
The following details can be obtained from the OpenID Connect metadata document URI.
- Response Types Supported
sso-azuread-response-type - Response Modes Supported
sso-azuread-response-mode - Issuer
sso-azuread-issuer - Scopes Supported
sso-azuread-scope
Deployment instructions
Step 1 Create a <secret-filename>.yaml file with the following template.
All the values must be base64 encoded
In mac you can run
echo -n "string to be encoded" | base64to get the encoded value
Step 2 Update the k8s secret in the namespace of that cluster using the above file.
Step 3 Update the Helm variable fiddler.auth.sso.provider and fiddler.auth.sso.azuread.secretName with azuread and fiddler-sso-azuread-credentials value. If you are using the helm values file, use the following settings.
Once the deployments are updated, the new SSO settings will be applied.
📋 Related articles
Detailed instructions for deploying an SSO-enabled cluster - Creating Multi-org w/ SSO enabled cluster in Dev | SSO enabled cluster
Updated 4 months ago
